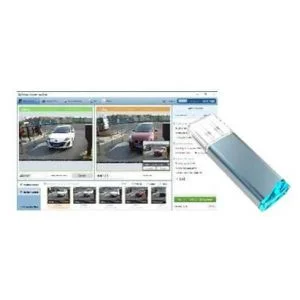
Access control and management systems (ACMS)
Access control and management systems (ACMS) are comprehensive solutions designed to manage and monitor access of people and vehicles to protected facilities, as well as to ensure security and automate entry and exit processes. These systems are widely used in office buildings, industrial facilities, educational institutions and other places where access control is required.
Main functions of ACS:
Access control:
ACS restricts or provides access to certain areas only for authorized persons.
Access can be provided using various technologies: access cards (RFID, magnetic cards), biometric data (fingerprints, face or iris scanning), code panels and mobile devices.
Time and attendance management:
ACS records the time of arrival and departure of employees, which helps to automate the calculation of working hours and control discipline.
Systems can generate reports for analyzing productivity and attendance.
Integration with other security systems:
The ACS can be integrated with video surveillance systems, security alarms and fire safety systems, creating a single solution for comprehensive protection of the facility.
Monitoring and recording events:
All events related to access are recorded in the system, which allows you to track and analyze the history of actions of employees and visitors.
In real time, administrators can control access to various areas and promptly respond to incidents.
Main components of the ACS:
Controllers:
Central devices that process information from readers and locks, control the opening of doors and other security systems.
Readers:
Devices that read information from access cards, biometric data or other identifiers. Readers can be contact (for magnetic cards) or contactless (RFID or NFC).
Locks and drives:
Electromagnetic or electromechanical locks controlled by a controller that lock or unlock doors when a signal is sent from the system.
Software:
Special software that allows you to administer the system, manage user access rights, track events and generate reports.
Turnstiles and barriers:
Physical barriers to restrict passage or travel. Turnstiles are used to control access for people, and barriers are used for vehicles.
Technologies used in ACS:
RFID cards and key fobs:
Contactless technologies for personal identification. Each card or key fob contains a unique identifier that is read by the system.
Biometric dаta:
Identification based on a person's unique physical characteristics, such as fingerprints, facial recognition or iris recognition.
Mobile technologies:
The ability to use smartphones and other mobile devices to access systems. For example, NFC or QR codes for contactless door opening.
Barcodes and QR codes:
Used for temporary access, for example, when issuing guest passes.
Advantages of ACS:
Security: Provides reliable protection of facilities, preventing unauthorized access.
Convenience: Automation of the entry/exit process, access control via various devices.
Control and accounting: ACS allows you to keep track of employee attendance, as well as create detailed reports on visits.
Integration: Possibility of integration with other security systems to improve the efficiency of facility management.
Application of ACS:
Offices and business centers: to control access of employees and visitors.
Industrial enterprises: to restrict access to work areas and control personnel movement.
Educational institutions: to control attendance of students and employees.
Parking and residential complexes: to control access of vehicles.
7ST-DM7750
Display: 10.1″ IPS touch screen, 1024×600 px Audio: built-in microphone and speaker, two-way audio, noise and echo suppression, codecs
1,633,500 uzs
7ST-S1T771MF
Device type: Wall-mount access control terminal Camera: 2 MP wide-angle, face recognition (0.3–3 m) Video formats: H.264, MJPEG Video
2,711,500 uzs
7ST-SV6113-WPE1
Camera: 2 MP HD Video: 1920×1080p (1080p/720p), IR night vision, range ~3 m Field of view: Horizontal ~129°, Vertical ~75° Video
790,800 uzs
7ST-SB8113-IME1
Device type: IP surveillance camera Image sensor: 1/2.8" progressive CMOS Resolution: 4MP (2560×1440) Lens: 2.8 mm or motorized
732,000 uzs
7ST-KIT603-P
Device type: Video intercom kit (indoor monitor + outdoor door station) Monitor: 7″ color touchscreen, resolution 1024×600 px Camera: 2 MP
1,356,000 uzs
7ST-S1T543MFWX
Device type: Wall‑mount access terminal — flat panel Camera: 2 MP wide‑angle, face recognition at 0.3–1.5 m distance Video formats: H.264,
1,037,500 uzs
Hikvision DS-TPE002
Model: DS-TPE002 Type: ESD wrist strap tester Purpose: Real-time testing of ESD wrist straps used by personnel Display: LED indicators Test
2,015,000 uzs
Hikvision DS-PDMCK-EG2-WB(СМК+СВЧ)
Model: DS-PDMCX-E-WB Type: Wireless magnetic contact sensor (large size) Operating frequency: 868 MHz Communication distance: up to 800 m
416,000 uzs
Hikvision DS-KV6133-ME1
The DS-KV6133-ME1 is an advanced IP video intercom door station from Hikvision, designed for multi-apartment or office building use. Key
1,105,000 uzs
Hikvision DS-KIS902-S
DS-KIS902-S is a professional IP video intercom kit from Hikvision designed for high-quality video communication and remote access. The kit
3,380,000 uzs
Hikvision DS-K3G501BLX-R/Pg-Dm55
Model: DS-K3G501BLX-R/Pg-Dm55 Turnstile Type: Swing gate turnstile Material: 304 stainless steel + acrylic wing Throughput Rate: 30–40
17,550,000 uzs
Hikvision DS-K6B411TMX R TURNIKET
Model: DS-K6B411TMX M (middle module) Turnstile Type: Glass turnstile – middle section Material: 304 stainless steel + glass panels
19, 500,000 uzs
Hikvision DS-K6B411TMX M TURNIKET
Model: DS-K6B411TMX M (middle module) Turnstile Type: Glass turnstile – middle section Material: 304 stainless steel + glass panels
26,000,000 uzs
Hikvision DS-K6B411TMX L TURNIKET
Model: DS-K6B411TMX L (Left Side) Turnstile Type: Glass Turnstile Material: 304 Stainless Steel + Glass Panels Passing Rate: 30–40
19, 500,000 uzs
Hikvision DS-K3B411BX-Dp65/2
Model: DS-K3B411BX-Dp65/2 Type: Speed pedestrian swing barrier gate Material: SUS304 stainless steel, acrylic swing panels Sensors: 6
910,000 uzs
Hikvision DS-PDP18-EG2
Specification Description Model DS-PDP18-EG2 Type Outdoor PIR Motion Detector Detection Range 18 meters Detection Angle 90° Power Supply
117,000 uzs
Hikvision DS-PK-LRT
Feature Specification Model Hikvision DS-PK-LRT Type Remote Control Panel Power Supply 3V (Lithium Battery) Battery Life Up to 5 years
546,000 uzs
DS-PDP15P-EG2-WB (Движение+СВЧ)
Feature Specification Model DS-PDP15P-EG2-WB Type Wireless Motion & Microwave Detection Sensor Detection Method PIR + Microwave
429,000 uzs
DS-PDMCX-E-WB
Feature Specification Model DS-PDMCX-E-WB Type Wireless PIR Motion Detector Detection Range 12m (39.37 ft) Detection Angle 110° Detection
416,000 uzs
Hikvision WiFi Router Linkff FF-AP3A
Model: Hikvision WiFi Router Linkff FF-AP3A Wi-Fi Standard: 802.11a/b/g/n/ac Frequency Range: 2.4 GHz / 5 GHz Maximum Speed: 1200 Mb/s
130,000 uzs
Hikvision DS-3WF02C-5AC/O
Specifications English Model Name DS-3WF02C-5AC/O Type Wireless Access Point Frequency Bands 2.4 GHz / 5 GHz Wi-Fi Technology Wi-Fi 5
923,000 uzs
Geri
1 2 3 4 5 6 7 8 9
İrəli